With the continuous development of security protocols, I have come to understand that the prevention system of Wireless Intrusion Prevention Systems (Wireless IPS) is extremely important for all people who are looking for a way to protect their network against cybercriminals. A Wireless IPS is a special device designed to watch and prevent unauthorized connections to wireless networks and different kinds of attacks.
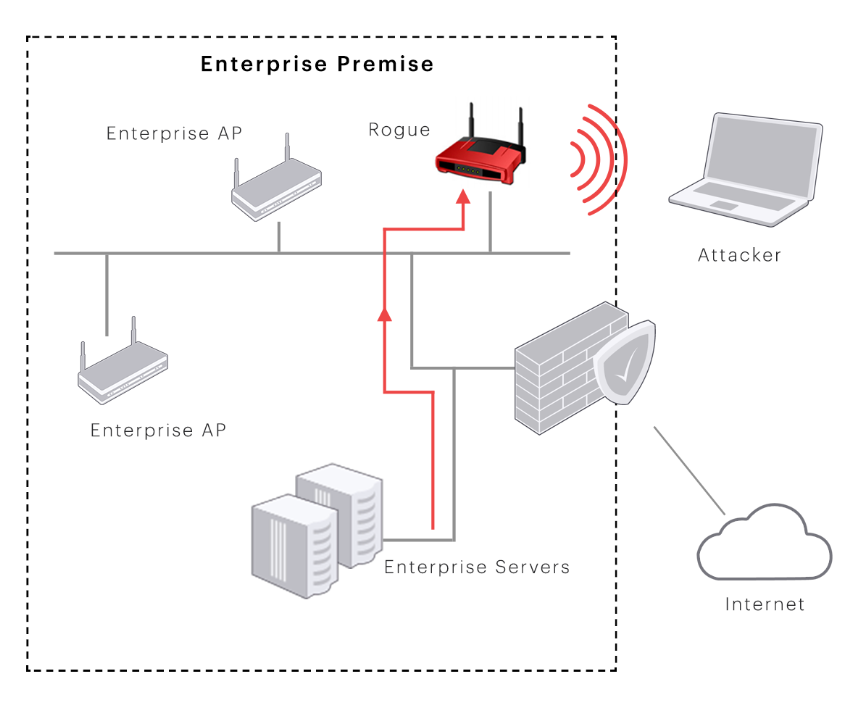
Unlike traditional intrusion detection systems, which only alert the administrators about potential threats, a Wireless IPS actively does the things necessary to prevent those threats from coming into existence. The proactive strategy involved in this style of defense is of intrinsic importance since cyber threats keep getting more advanced and widespread. However, as I dig deeper into the topic, I realize that these systems consist of both hardware and software to detect irregularities in wireless traffic. The systems are essentially analyzing attitudes and behaviors, from which they are constantly learning something different than when an unauthorized person is trying to sneak in with bad intent.
These techniques which are e.g. signature-based detection, anomaly detection, and policy enforcement can be applied to a Wireless IPS in order to manage the wireless network risks. Consequently, I am better-equipped to weigh the security implications of different options and thus make an informed choice about setting up my own network.
Identifying the Risks of Unsecured Wireless Networks
Consequences of Unsecured Networks
This can result in data breaches, identity theft, and even financial loss. The problem of data security brought about by an open network is the ease with which an unauthorized person can establish a connection, which not only raises concerns but also makes it clear that it is a dead serious thing.
Vulnerabilities to Attacks
Furthermore, I have comprehended that the non-secured wireless local area networks (WLANs) are the victims of different hacking techniques like man-in-the-middle attack and eavesdropping. At this point, it should be noted that a man-in-the-middle attack is an attack in which we neither user knows that the attacker is intercepting the communication. Subsequently, a witness is then able to document or overhear such confidential conversations and retrieve sensitive data.
The Importance of Wireless IPS
These dangers make it clear that we have to put our efforts into keeping our WiFi secure, and Wireless IPS could be the part of this effort.
Implementing Wireless IPS Solutions
Deployment of Wireless IPS solutions is a very delicate process that, however, involves careful planning and study. Honestly, the best way to start is by doing an accurate assessment of the current wireless network infrastructure. The topic of the day here is to pinpoint all the potential loopholes and define the business-related security needs. After checking the safety status, I can easily conclude the effectiveness of the implementation of a Wireless IPS into my company’s network. I will also point out the weaknesses in the infrastructure of the system so that we can select the most appropriate intervention that coherently satisfies our security strategy. Furthermore, I can assist with a suitable Wireless IPS solution if we get into a mess with the deployment. In such a situation, the system configuration can be a complex task, and the steps we may choose for different deployments. An unfortunate system configuration can be a nightmare that may lead to performance issues. Thus, proper design remains the key factor to be considered for a reliable, efficient solution. I feel that the entire process of deploying, be it detection rules setup, the policy for treating threats, or the Wireless IPS software integrating into existing security tools, should be properly done. Successful deployment of a Wireless IPS system can be the best way to secure your wireless network, thereby eliminating your worries over how dangerous the digital world has lately become.
Choosing the Right Wireless IPS Solution for Your Network
Wireless IPS Solution Features Benefits Vendor A Real-time monitoring, threat detection, centralized management Enhanced security, easy management, quick response to threats Vendor Advanced analytics, customizable alerts, integration with existing security systems, depth insights, tailored alerts, seamless integration Vendor C Cloud-based deployment, automatic updates, scalability Flexible deployment, up-to-date protection, adaptable to network growth.
Picking the right Wireless IPS solution is an important decision that can greatly affect the security of my network. No matter how many options I have to choose from in the market, I should consider more than one aspect of every one of them before I make a choice. The fact that one of the most pressing issues is how scalable it is; my company’s size evolves, and network traffic grows. A method that I can adjust to the upswing of traffic and new gadget additions without security getting worse is the one what I need most. Moreover, convenience should be the other most important aspect. I prefer to use solutions where the interfaces are user-friendly and the management tools are simple. A system that is too complicated may cause me not to react fast to the issue or even administer security policies inefficiently. On the other hand, I also need to check the support at the vendor’s level. Having found a customer-oriented team that provides prompt solutions and assists with configurations and management, I see the value of customer support.
Best Practices for Securing Your Network with Wireless IPS
To maximize my Wireless IPS’s efficiency, I see that the strict following of the best practices is necessary. One of the main practices that is suggested is the frequent updates of the system software and the threat signatures. The cyber threats are transforming constantly, so I have adopted the practice of always having my Wireless IPS updated so that it can easily distinguish any new vulnerabilities and respond to them immediately. By following this proactive procedure, the threat of lions may become almost nonexistent. On the other hand, one of the best practices that an entity can adhere to is to systematically carry out security audits and assessments. Certainly, through these tests of my security posture, I can discover any breach or inconsistency that requires improvement. This method not only allows me to keep up with the standard in the industry but also adds strength to my security strategy. Also, teaching the employees about wireless security practices is very important as they are usually the first line of defense against such kind of potential threats.
Monitoring Your Wireless IPS and Guaranteeing Its Management Security
Real-Time Monitoring for Threat Detection
To me, real-time monitoring is the best way of detecting potential threats as soon as they occur. Most Wireless IPS vendors offer a dashboard that shows network activities in real-time, which enables one to quickly identify any strange patterns or behaviors.
Staying Attentive through Log Analysis
To stay on top of problems and in the focus of my attention, I have to be always alert and strictly monitor my network. Apart from instant detection, I also need a habit of checking logs and the reports processed by my Wireless IPS. These traces are very helpful in identifying the causes of the detected threats and also in estimating the performance of the systems and user activities.
Maintaining a Comprehensive View of Network Security
See and understand immediately the shifts in the network behavior and spot where security needs enhancements. To be able to look at the security of the network from different perspectives, real-time monitoring and regularly analyzed logs should be merged.
Responding to Security Threats with Wireless IPS
Of course, depending on the context, a properly planned recovery could be the key to a speedy reaction and the complete restoration of functions. My Wireless IPS device also comes with automatic responses that take care of the threats that I detect. Suppose, for example, that a device not associated with me seeks to link to my LAN, then the system can, by itself, keep such an unauthorized device at bay, and, this way, no breaches will happen. Nevertheless, I realize the significance of humans in the process as well as in identifying and responding to complex threats. In case of such situations, I should be prepared to gather information about the incident in full and select a suitable strategy of action. This may involve isolating the infected system(s), performing the forensic analysis, or contacting the police. Combining smart machine learning and educated decision-making, I can efficiently solve security issues and save my network from trouble.
Future Trends in Wireless IPS Technology
Thinking of the Wireless IPS technology in the future, I am looking forward to several upcoming technologies that will improve the security of the networks even further. One of these encouraging issues is the incorporation of AI and ML technologies into Wireless IPS solutions. They are programmed to acquire the ability to detect patterns through examination of data and then, in turn, apply those attainments. About the effectiveness of these AI-generated IPS, they are not only very effective in correctly recognizing and responding to new complex threats, but also are better suited than conventional systems. Another trend that is worth mentioning is the fact that cloud-based Wireless IPS has become the center of attention in recent years. As an alternative to the users’ on-premise facilities, a cloud-based wireless IPS offers the reduction of costs and the profit from the strengths of the cloud environment, i.e., scalability and flexibility, along with the best possible protection. I, thus, expect to see these tools as the majority of the new tech coming forward for wireless network security. In brief, being aware of Wireless IPS is a must for anyone wanting to gain adequate protection of their wireless networks from cybersecurity threats. To this end, knowing the potential hazards that exist in the unsecured network and taking preventive measures as well as assessing the most effective ways to protect the necessary applications in a specialized way are the steps that will serve me to the best protection of the network’s security. Along with the advancement of technology, being well-informed about the latest Wireless IPS trends will be the ultimate provision for adapting to the new risks in cybersecurity.
FAQs
What is a wireless IPS (Intrusion Prevention System)?
Wireless IPS, a security system, is one that gives security on a wireless network by monitoring and analyzing unauthorized traffic.
How does a wireless IPS work?
A wireless IPS operates by constantly tracking the traffic of wireless networks, analyzing suspicious activities, and taking action to stop threats, for example, blocking of the unauthorized devices or traffic.
What are the benefits of using a wireless IPS?
Improved network security, protection against unauthorized access and attacks, real-time threat detection, and compliance with security regulations and standards are several benefits of a wireless IPS.
What are some common features of a wireless IPS?
Typical services of a wireless IPS include intrusion prevention, intrusion detection, rogue device detection, wireless traffic analysis, and reporting and alerting capabilities.
What are some best practices for deploying a wireless IPS?
Best practices for deploying a wireless IPS include making a precise inventory of the wireless network environment, setting up the system to monitor and protect the core assets, and regularly updating and maintaining the IPS to guarantee optimal performance.







